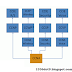
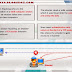
An Introduction to XSS In this tutorial I will not be going into depth of XSS, I will be covering the explanation of the basic types. ...
Create Free Website Instant
Hey Guys ! Here are some Best networks where you can create free Instant Website Without any Skillful knowledge about designing and dev...
Increase Page Views | Web Hits Flooder
I am going to show you how to increase the page hits of you website.For this you want to dedicate a browser .In this i am using interne...
Turn KeyBoard to Disco keyBoard
This trick just makes your keyboard lights go crazy and do disco. The script I’m sharing with you, when executed makes your Caps, Num a...
RFI - Remote File Inclusion - web Hacking
Hello Guys ! today I'm going to show you how RFI process goes Step By Step #Searching for Vuln. Sites #Checking if they are V...
RAT - Introduction
RAT stands for Remote Access Trojan or Remote Administration Tool. It is one of the most dangerous virus out their over the internet. Hac...
Internet Download Manager - Full Version - Registered
Latest Internet Download Manager Registration Internet Download Manager is a full-featured package that handles downloading tasks with a...
Turn your Laptop into Wi-Fi hotspot ! Share Wifi |
Sometimes, we need to access shared internet or want to share our internet with other people. At that situation we don’t have the sui...
How to Become a Good Hacker
What are the things that you need to become a hacker? 1. Programming Knowledge: → C/C++ → Web designing (HTML/CSS,Javascript,PHP,...
CCNA Network Devices - CCNA Basic
Guys i am here with New Topic! Cisco Network Devices ♦ Router ♦ Routers are networking devices that forward data packets between net...
Access any PC without knowing the password
Guys i am sharing great Tool with you :) known as KON-Boot Rather than cracking a Windows password, KON-BOOT bypasses it and lets...
Useful Websites For Hacking
To check if a port is open: http://www.canyouseeme.org/ To multiple scan a file for viruses: http://vscan.novirusthanks.org/ The best...
List of Web Application Hacking methods
Below are the well known Methods For Hacking Web Applications ! This list below fits in category Parameter manipulation Arb...
Animated Heart Share Buttons Blogger Widget
Hey Guys i am here With New Tutorial. This is Animated beautiful Heart Widget with Social Buttons ! Lets see how to add it to your bl...
Fixed Social Media Widget For Blogger
Hey Guys ! i am gonna show You how to add Social media Bar "Static Social Media Widget" On your Blog! Its ...
Basic Of networking | CCNA
What is a computer Network? A network is any collection of independent computers that communicate with one another over a shared netw...
Introduction To CCNA
Asalam-O-Alykum Guys !! I am Raheel and This is Our First Lecture About CCNA ! Defination : CCNA (Cisco Certified Network Associate) ...
Free CCNA Course
Assalam-O-alykum ! Hope you all Ok ! So guys i m starting New CCNA R/S " Cisco certified Network Assosiate 'Route/switch' ...
Android Apllications on Pc
Do you wish to run Android application or games but don’t have a Smartphone to do it? Do you want to use Instagram on Pc and want to play ...
Create PDF of Any Website
If you want to save web pages in a PDF file then you should follow the following steps you can use the PDF file while you do not have acces...
Flip Text Upside Down
Want to surprise your friends on Facebook, Twitter , My Space or Google Plus? Write Your Text Here ! and Flip Your Text :) Make...
Session Hijacking
Session hijacking refers to the exploitation of a valid computer session where an attacker takes over a session between two computer...
Penetration Testing
What is Penetration Testing? Penetration testing is the legal and authorized attempt to exploit a computer system with the intent of...
Linux Distributions
Hey Guys I am here Again Today i m gonna Share information about Linux Distro' ! There are many Distro' . Here is a Short Introduc...
Linux Introduction
What is Linux? Linux is an operating system that evolved from a kernel created by Linus Torvalds when he was a student at the Univ...
Hacking DNN website | Portal Hacking |
Hey Guys , One more hacking method called "Portal Hacking " DOT NET NUKE" (DNN)". This method also uses google search ...
SQL Injection Basic Hacking TuT
If you are new to the world of hacking websites, then SQL injection is possibly the easiest to learn and most common of the substan...
Hacking Facebook in LAN
in this post I am going to show you a way you can hack the facebook accounts of all the people who are on your network (LAN or wifi ) . I ...
EC Council - Penetration Testing Procedures & Methodologies
Hey Guys ! EC Council Book For you !! This Book is about Penetration Testing ! Download and Read ! This book discusses the vario...
Sql Injection Dork List
Today i am gonna share Google Dorks for sql injection ' which is one of the most used method to hack a website . Using the SQL...
Find Facebook Profile ID
Here is the trick which will let you get profile id of any person who got custom username. You can also Find Fan Pages Id . Check below ima...
Disclaimer
Disclaimer These articles are intended for IT Professionals and systems administrators with experience servicing computer hardware. Ple...
| About Me |
Well About me.. I am in search Of my Self " Apni Talash mein " ! Neither Noob , Nor Geek ! Currently learning loads ...